Summary
Microsoft zero-day vulnerabilities in 2026 continue to pose immediate risk because they are exploited before official patches are available. These flaws often affect widely deployed platforms such as Windows, Microsoft 365, Azure services, and on-premises enterprise infrastructure. Effective defense depends less on reactive patching alone and more on layered mitigation, rapid detection, and disciplined operational response.
Why Zero-Day Risk Feels Different in 2026
A familiar pattern continues to unfold across enterprise environments: a routine system runs as expected in the morning, and by afternoon, indicators of compromise surface tied to an exploit no vendor bulletin has yet addressed. The defining characteristic of Microsoft zero-day vulnerabilities is not just technical severity—it is timing. Organizations are forced to defend systems during a window where adversaries may have a capability advantage.
In 2026, this dynamic has intensified. Cloud-connected ecosystems, hybrid identity models, and AI-accelerated attack tooling have shortened the gap between vulnerability discovery and weaponization. What many discussions still oversimplify is this: the true damage rarely stems from the initial exploit alone. Instead, the downstream impact—credential theft, lateral movement, domain dominance, or data staging—creates the real operational crisis.
Security leaders who treat zero-days as isolated patching events often underestimate how these exploits interact with identity infrastructure, endpoint configurations, and security tooling gaps.
The Expanding Microsoft Attack Surface
Microsoft’s ecosystem spans operating systems, productivity platforms, identity services, development environments, and cloud workloads. A single vulnerability in one layer frequently cascades across others.
In 2026, several structural shifts amplify exposure:
- Deep integration between Windows endpoints and cloud identity services
- Increased reliance on remote management tools
- Widespread use of PowerShell automation and administrative scripting
- Hybrid Active Directory and Entra ID configurations
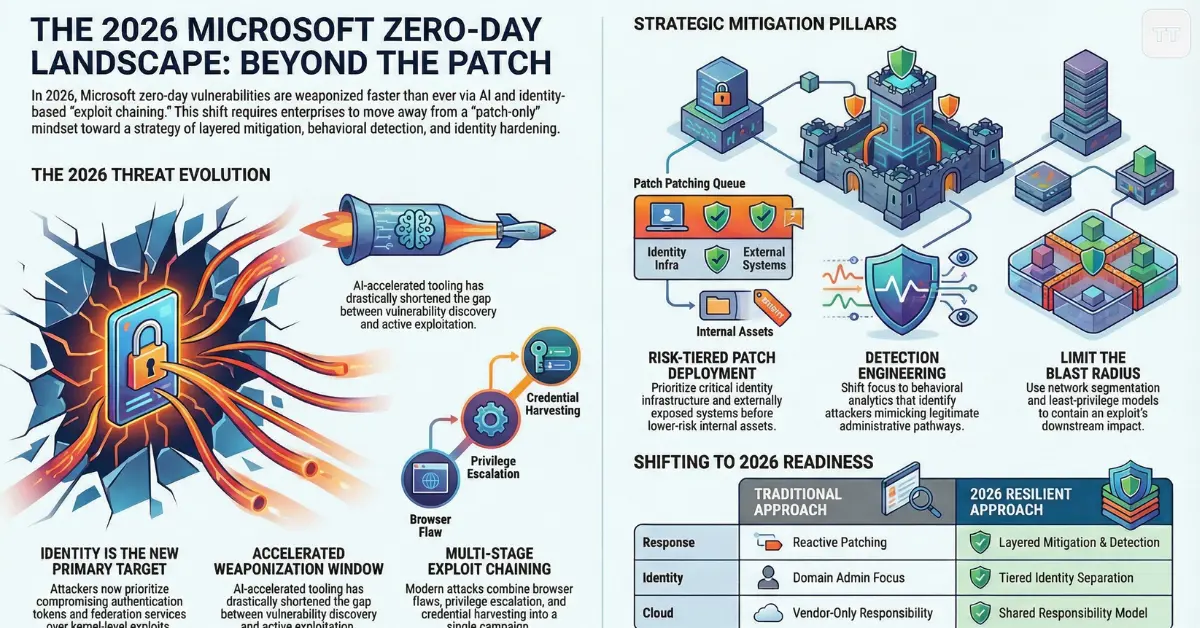
Active zero-day attacks on Microsoft products increasingly target identity pathways rather than kernel-level exploits alone. Compromising authentication tokens, federation services, or privileged service accounts offers attackers durability and stealth.
A notable shift in Microsoft zero-day exploit 2026 campaigns involves chaining vulnerabilities. An attacker may combine a browser memory flaw with privilege escalation in Windows, followed by credential harvesting against directory services. This multi-stage model challenges traditional perimeter thinking.
How Zero-Day Exploits Are Weaponized Today
Zero-day exploitation has become operationally industrialized. Threat actors no longer rely exclusively on custom-built exploit kits; instead, they leverage:
- Rapid vulnerability reverse engineering from patch previews
- AI-assisted fuzzing techniques
- Exploit marketplaces and brokered vulnerability sales
- Targeted spear-phishing delivering exploit payloads
The misconception that zero-days are rare and nation-state exclusive is increasingly outdated. While sophisticated actors still dominate early discovery, financially motivated ransomware groups often obtain exploit access within weeks—or even days—through underground channels.
An overlooked reality is that many zero-day breaches succeed not because the vulnerability is technically complex, but because detection engineering lags behind exploit innovation. Signature-based detection often fails during the early exploitation window.
Patch Tuesday Is No Longer the Whole Story
Microsoft Patch Tuesday vulnerabilities still serve as the backbone of enterprise patch cycles. However, the assumption that risk peaks only on scheduled release days is flawed.
Zero-days introduce asymmetry:
- The vulnerability may be exploited weeks before public disclosure.
- Security teams may only recognize compromise after patch release highlights the flaw.
- Exploits often persist post-patch due to incomplete remediation.
Windows zero-day security patches frequently address memory corruption, privilege escalation, or remote code execution flaws. Yet patch deployment does not immediately eliminate risk. Systems may remain exposed due to:
- Delayed rollout in operationally sensitive environments
- Unsupported legacy systems
- Third-party application dependencies blocking updates
One critical but under-discussed issue is rollback exposure. If an emergency patch causes instability and is temporarily withdrawn, organizations may revert systems—reintroducing exploitability during an already active threat cycle.
Security maturity in 2026 means treating Patch Tuesday as a checkpoint, not a safety guarantee.
The Tradeoffs of Rapid Patching
Immediate patching appears ideal in theory. In practice, enterprises face complex tradeoffs.
Rapid deployment may:
- Disrupt production systems
- Break application compatibility
- Interfere with regulated environments requiring change approvals
Delayed patching increases exposure but preserves operational stability. The decision is not binary. Advanced organizations now rely on risk-tiered deployment:
- Critical externally exposed systems patched first
- High-value identity infrastructure prioritized
- Lower-risk internal assets staged after validation
Enterprise zero-day threat mitigation must balance uptime, regulatory constraints, and threat intelligence. Blanket “patch immediately everywhere” policies can cause cascading business disruptions, particularly in healthcare, finance, and industrial sectors.
The more strategic approach involves pre-built emergency change pathways—governance structures that allow accelerated patching without bypassing accountability.
Detection: The Often-Weaker Link
The uncomfortable truth is that many enterprises discover zero-day exploitation through external notification—law enforcement, threat intelligence partners, or customer impact—rather than internal detection.
Why?
Because zero-days frequently exploit legitimate administrative pathways. Attackers mimic standard PowerShell execution, token usage, or service account activity. Without behavioral analytics tuned to anomaly detection, these activities blend into normal noise.
In 2026, leading SOC teams emphasize:
- Identity anomaly monitoring
- Endpoint detection and response telemetry correlation
- Privileged account behavior baselining
- Memory-level forensic collection
An insight often missed: organizations that invest heavily in patch speed but neglect detection engineering may still suffer prolonged dwell time. Patching stops new exploitation but does not remove already established persistence mechanisms.
Identity Infrastructure: The True Battleground
A recurring theme in Microsoft zero-day vulnerabilities involves privilege escalation tied to identity services. Whether targeting Kerberos delegation flaws, token forgery weaknesses, or directory synchronization gaps, attackers understand that identity equals control.
In hybrid environments, synchronization bridges between on-premises Active Directory and cloud identity platforms introduce complexity. A vulnerability exploited in one layer can propagate trust relationships elsewhere.
Defensive posture should prioritize:
- Least-privilege administrative models
- Just-in-time access provisioning
- Tiered identity separation
- Monitoring of domain controller activity
Organizations that still rely on broadly scoped domain admin accounts create disproportionate blast radius when a zero-day exploit grants elevated privileges.
Cloud Services and the Shared Responsibility Misconception
Cloud-hosted Microsoft platforms introduce a subtle misunderstanding. Some decision-makers assume that vendor-managed infrastructure eliminates zero-day risk.
In reality, the shared responsibility model means:
- Microsoft secures the underlying platform
- Customers secure configurations, identity, and data access
If a zero-day affects a SaaS service, Microsoft may patch backend infrastructure quickly. However, if exploitation targets tenant misconfiguration or overly permissive API integrations, the vulnerability may persist at the customer layer.
The distinction between platform-level and tenant-level exposure becomes critical during active zero-day attacks on Microsoft products.
Incident Response During Active Exploitation
When a Microsoft zero-day exploit 2026 scenario becomes public, the first 48 hours define impact scope.
Effective response includes:
- Immediate vulnerability exposure assessment
- Log preservation before system reboots
- Isolation of suspected compromised assets
- Rapid credential rotation for privileged accounts
- Threat hunting across identity and endpoint telemetry
A common mistake is focusing exclusively on patch confirmation without investigating pre-patch compromise. Forensic validation must accompany remediation.
Organizations with predefined playbooks significantly reduce chaos during these windows. Those without them often experience internal communication breakdowns that delay containment.
Strategic Mitigation Beyond Patching
Enterprise zero-day threat mitigation requires layered controls that assume exploitation will eventually occur.
Critical strategies include:
- Network segmentation limiting lateral movement
- Application allowlisting to restrict arbitrary code execution
- Multi-factor authentication resistant to token replay
- Immutable backups protected from domain compromise
- Conditional access policies tied to device health
One overlooked mitigation is configuration hardening against exploit chaining. Many zero-days become devastating only when combined with weak privilege controls or exposed administrative interfaces.
Zero-trust architecture principles—when implemented realistically rather than marketed aspirationally—significantly reduce zero-day impact.
What Competitors Often Ignore: Post-Patch Exposure
Most public discussions end once a Windows zero-day security patch is deployed. However, post-patch exposure introduces subtle risk.
Attackers frequently analyze patches to reverse engineer the vulnerability. Organizations that delay deployment effectively broadcast that they remain exploitable.
Additionally, exploit attempts often surge immediately after public disclosure. Threat actors know many enterprises require days or weeks to deploy updates.
This means that the most dangerous window may not be pre-disclosure—but immediately after.
Security leaders who understand this pattern often increase monitoring intensity during the first week after patch release.
Evaluating Organizational Readiness
Not every organization requires the same defensive depth. Context matters.
High-risk profiles include:
- Financial institutions handling transactional data
- Healthcare networks with sensitive patient records
- Critical infrastructure operators
- Technology providers hosting customer environments
Lower-risk organizations may still face ransomware impact but may prioritize business continuity over high-complexity identity segmentation.
Decision-makers must evaluate:
- Asset criticality
- Threat actor interest level
- Regulatory consequences
- Operational resilienceMicrosoft Zero Day
Mature organizations integrate zero-day planning into annual tabletop exercises rather than reacting only when headlines emerge.
Frequently Asked Questions
What is a Microsoft zero-day vulnerability?
A Microsoft zero-day vulnerability is a software flaw that is actively exploited before an official security patch is available. Because defenders have “zero days” to prepare, attackers gain a temporary advantage until mitigation or patching occurs.
How do zero-day exploits differ from regular vulnerabilities?
Zero-day exploits are weaponized before public disclosure or patch release. Regular vulnerabilities are typically identified, disclosed, and patched before widespread exploitation occurs.
Are Windows zero-day security patches enough to stop attacks?
Patching stops new exploitation, but it does not remove existing compromise. Organizations must also investigate persistence mechanisms, rotate credentials, and validate system integrity.
How can enterprises prepare for active zero-day attacks on Microsoft products?
Preparation involves layered defenses such as segmentation, identity hardening, behavioral monitoring, and incident response planning. Rapid detection and controlled patch deployment reduce operational disruption.
Do Microsoft Patch Tuesday vulnerabilities include zero-days?
Sometimes. Patch Tuesday releases may include fixes for vulnerabilities that were exploited in the wild prior to disclosure, effectively converting a zero-day into a patched vulnerability.
Is cloud infrastructure safer from zero-day threats?
Cloud platforms may receive faster vendor-side patching, but tenant misconfiguration and identity weaknesses still expose organizations. Shared responsibility means customer security controls remain critical.
Conclusion: Rethinking the Zero-Day Mindset
Microsoft zero-day vulnerabilities in 2026 are less about technical surprise and more about organizational readiness. The exploit itself is only the opening move. The decisive factor is whether detection, identity governance, segmentation, and response planning limit escalation.
Enterprises that treat zero-days as inevitable but containable events tend to recover faster and suffer less reputational damage. Those that rely solely on patch cycles often discover that vulnerability management without architectural resilience provides only partial protection.
The future of zero-day defense lies not in predicting every flaw—but in building environments where a single exploit cannot define the outcome


